Authorities in South Korea have arrested four individuals in connection with a massive hacking operation that breached roughly 120,000 internet-connected surveillance cameras installed in homes and businesses.
The hacked devices were mainly IP cameras, network-connected home and business units commonly used to monitor children, pets, security, and daily activities. Hackers easily breached these cameras by exploiting weak security settings, as many owners still used simple or default passwords such as repeated or sequential numbers. Investigators found that the four arrested suspects were not part of a coordinated group; instead, each operated independently while carrying out the hacks and creating illicit recordings. korea joongang daily
Extent of the exploitation
Police revealed that the four arrested hackers operated independently, not as a coordinated group, and collectively breached over 120,000 IP cameras across South Korea. One suspect allegedly hacked 63,000 cameras and produced 545 sexually exploitative videos, which he sold on a foreign adult website for about ₩35 million in cryptocurrency. In contrast, another hacked 70,000 cameras, created 648 videos, and earned roughly ₩18 million from sales. Together, their footage accounted for an estimated 62% of all illicit uploads on the targeted adult platform over the past year. The remaining two suspects compromised around 15,000 and 136 cameras, respectively. Still, investigators found no evidence that they distributed or monetized the recordings, highlighting how a mix of large-scale and more minor opportunistic breaches contributed to one of South Korea’s most widespread digital-privacy crimes.
South Korea’s National Police Agency (NPA) has launched a wide-ranging investigation targeting not only the hackers behind the camera breaches but also the foreign website distributing the illicit videos and the individuals who viewed or purchased the content. Authorities have already contacted 58 affected locations—including homes, clinics, studios, and small businesses—to notify victims, help secure their devices by resetting passwords, and work with the Digital Sexual Crime Victim Support Center to remove or block exposed footage. Police officials stressed that under South Korean law, simply viewing or possessing illegally filmed material constitutes a serious criminal offense, underscoring the gravity of both the breaches and their downstream exploitation. bleepingcomputer

Why this case highlights a global problem
The incident exposes a widespread global issue: IP-based home and business cameras have become extremely common because they are cheap, easy to install, and accessible through mobile apps. However, many are deployed with weak or default passwords, outdated firmware, or unsecured remote-access settings. This creates a perfect entry point for cybercriminals, who can scan the internet for vulnerable devices, breach them at scale, and exploit the footage for financial or sexual abuse.
Three Key Solutions
- Enforce Strong Security Defaults
Manufacturers and users must eliminate default or simple passwords, enforce strong credential requirements, and enable two-factor authentication. This reduces unauthorized access dramatically. - Regular Firmware Updates & Secure Configuration
Cameras should receive automatic security patches, have remote access disabled unless necessary, and be protected behind firewalls. Proper configuration closes many of the vulnerabilities hackers rely on. - Continuous Monitoring for Leaks, Exploits, and Dark-Web Activity
Organizations and product manufacturers should monitor the open web, deep web, and dark web for leaked IP camera credentials, exploit kits, or lists of vulnerable models being traded or requested by threat actors.
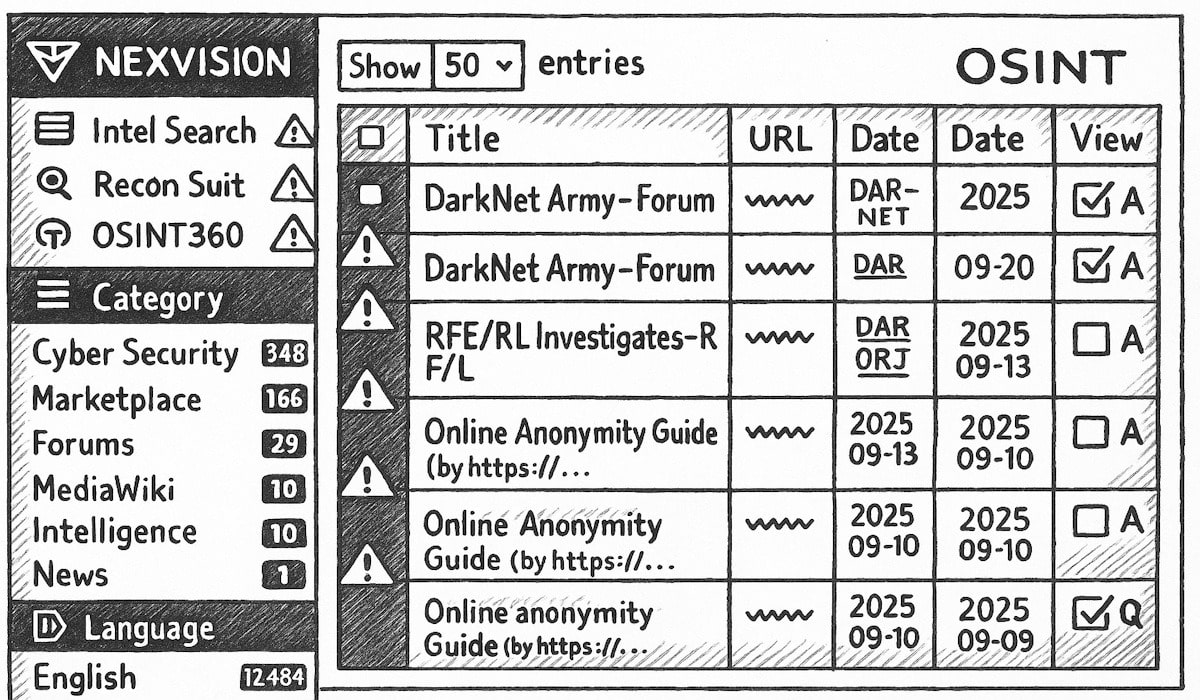
How NexVision OSINT Helps
NexVision’s OSINT and dark-web intelligence platform strengthens these solutions by:
- Identifying leaked credentials, access tokens, or camera passwords circulating on cybercrime forums, marketplaces, Telegram channels, and dark-web markets—allowing organizations to act before attackers exploit them.
- Detecting exploit discussions and vulnerability requests, such as “looking for IP camera access,” “firmware exploit kits,” or “lists of Korean/Asian IP cams,” giving early warning of emerging threats targeting specific vendors or regions.
- Providing real-time monitoring and alerts, enabling security teams, manufacturers, or government agencies to take immediate action by forcing password resets, issuing patches, or warning affected customers.
With NexVision, organizations gain the ability to spot attacks before they happen, reduce exposure, and protect users from large-scale privacy breaches like the South Korea camera hacking case.






